Athena Dynamics Young Writer’s Series Article #7: Diving into Deepfake Phishing Attacks
Athena Dynamics Young Writers Series: Diving into Deepfake Phishing Attacks
Author: Bryan Lee, Business Development Intern, Athena Dynamics
Advisory Editor: Nyan Tun Zaw, VP of Business Development, Athena Dynamics
Copyright © December 2021 All Rights Reserved Athena Dynamics Pte Ltd
What is its purpose?

Like any cyber-attacks, voice phishing is most commonly carried out to achieve financial gains. Victims could be scammed out of their bank account numbers and password, giving attackers access to the victim’s savings. Identification information such as NRIC or social security number are also an attacker’s target as these can be sold for money on the black market.
Identification information can be further used to disguise the attackers with the stolen identity and fool more victims or use it to perform malicious activities online to hide their identity.
What are the different types of voice phishing?
Here are 3 most common types of voice phishing methods:
Wardialing
This involves the use of technologies to make multiple calls in a specific area code. If a person picks up and answer the call, an automated message will be played. This message may involve banks requesting for login credentials or the police demanding a fine to paid over the call.
VoIP
This method allows anonymity of the caller by allowing them to use fake numbers when making calls. This makes it difficult to track the source of the call, allowing the attacker to continue with their malicious act without being caught. In this instance attackers may disguise themselves as government agencies, threatening a lawsuit if they do not pay up.
Dumpster Diving
This final method is simple to execute and allows the attacker to put on a decent disguise. This involves the attacker going through a company’s dumpster and finding for documents containing phone numbers. As the phone numbers are mostly belonging to legitimate people or businesses, attackers will use these numbers to fool unsuspecting victims into thinking they are talking into the real businesses. They will hence give out sensitive and personal information to the attackers.
How is the attack carried out?
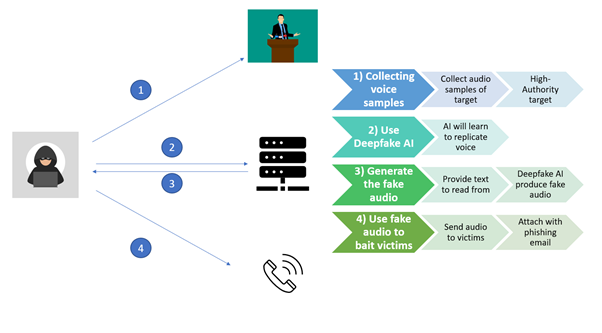
The following steps will explain the steps taken perform a voice phishing attack. These steps are a more advanced methods of performing the attack as it uses Deepfake technology to produce the fake recording. Below is a diagram to sum up the 4 steps of this scam.
1) Collecting voice samples
First, the attacker has to collect voice recordings of a person they want to impersonate. In most cases, they will use a person with high authority in a company or country such as the CEO or the president. This will make the recording generated more credible and believable to the victim.
These voice samples can be collected from speeches, interviews, or meetings where the attacker can record and isolate the person’s voice. It is important to record as many samples as possible as this will provide the AI with a large array of audio to learn from to better match the voice of the person.
2) Running it through a program that learns the voice
Next, the attacker will take these recordings and run them through a voice cloning program. This program will take the recordings and learn the unique features of the person’s voice such as pitch, intensity, and tone. As each person has distinct features in their voices, the Deepfake AI can produce a voice replica specifically based on the audio recordings provided.
Currently, there many of such software that can perform voice cloning, but mainly with the intentions of using it for voice and video editing.
3) Providing text to generate the fake audio
Afterwards, the attacker just has to type in the text that they want the voice to say. The Deepfake AI will use the voice that it has just learned and apply them to the new text that it is given. The message could be an urgent need of money by the boss or a simple request for login credentials from the bank.
After running the software, this will finally give the attackers the fake audio recording.
4) Use the fake audio to bait victims
Now, the attacker will deliver this recording to the victims wait for them to fall prey to it and provide the information the attacker wants. The delivery could be carried out over a phone call where the attacker calls the victim using a fake number and play the audio recording; Or the recording could be attached to an email that is sent to the victims, alongside a phishing email.
How to protect yourself against voice phishing attacks?
Here are some steps you can take to keep yourself safe from Voice Phishing Attacks:
- Remain Vigilant when picking up phone calls
- Check the credentials of the caller when they request for sensitive information
- Be careful when giving out sensitive information
- Be alert when the caller ID is unknown, or number is not recognisable
Cybersecurity awareness is very important as it can protect you and your close ones from online threats such as this. At Athena Dynamics Academy, we ensure all participants are fully equipped with the latest cybersecurity knowledge. Participants will be exposed to the latest Cyber Threats and explore malware prevention techniques, increasing their awareness against online threats. Do visit us at https://athenadynamics.com/academy/ or contact us at [email protected] for more information on how you and your team can be better equipped for the cyber world.
On a national level if you are in Singapore, for more information on how you can protect yourself against vishing scams and what to do when you have been scammed, visit the Scam Alert Website at https://www.scamalert.sg/ or call them at their hotline at 1800-722-6688.
Biographies
Bryan Lee is an Associate (Intern) in the business development team in Athena Dynamics Pte Ltd, a subsidiary of BH Global Corporation Ltd, a company listed on the Singapore Stock Exchange (SGX).
Contact: [email protected]

Nyan Tun Zaw is the VP of Business Development at Athena Dynamics Pte Ltd, which is a subsidiary of BH Global Corporation Ltd, an SGX mainboard listed company.
With a wide range of background in cybersecurity, software development, web development as well as networking, Zaw has in-depth experiences in deploying security solutions for several highly confidential government and critical infrastructure projects, particularly in the CDR/CDNR field as a technical lead. His interest mainly lies in Cybersecurity and AIML.
Zaw holds a Bachelor of Business Management, with double majors in Finance and Information Systems, from Singapore Management University as well as Master of Business Administration (MBA) from Quantic School of Business and Technology. He is also a holder of the Certified Ethical Hacker (CEH) and EC-council Certified Security Analyst (ECSA) certificates.
Being a technical person who also likes sharing his experiences and knowledge, Zaw has also been part of a speaking panels with global C-level executives at various events and conferences in the region.
Contact: [email protected]
Disclaimer: Neither BH Global, Athena Dynamics nor the writer guarantees full and timely accuracy of the write-up. Readers shall read with their own discretion, judgement and research if in doubt. If you wish to contribute further writings, please feel free to contact us.
Not for General Distribution. Copyright © 2021 All Rights Reserved. No part of this presentation materials may be distributed/reproduced without the writers’ expressed consent.
References
Federal Bureau of Investigation. (2020). Internet
Crime Report 2020. Federal Bureau of Investigation.
Iau, J. (9 February, 2021). The Straits Times.
Retrieved from Record number of scams in 2020 pushed overall crime rate in
S’pore to highest in more than 10 years:
https://www.straitstimes.com/singapore/courts-crime/record-number-of-scams-in-2020-pushed-overall-crime-rate-in-spore-to-highest
Seif, G. (2 July, 2019). Towards Data Science. Retrieved from You can now speak using someone else’s voice with Deep Learning: https://towardsdatascience.com/you-can-now-speak-using-someone-elses-voice-with-deep-learning-8be24368fa2
TerraNova Security. (n.d.). Terra Nova Security.
Retrieved from WHAT IS VISHING?:
https://terranovasecurity.com/what-is-vishing/