Cybersecurity Young Writers Series Article #2: Data Diodes Explained
Demystifying Data Diodes: Data Diodes Explained
Author: Bryan Lim, Business Development Intern, Athena Dynamics
Copyright © March 2021 All Rights Reserved Athena Dynamics Pte Ltd
Advisory Editor: Nyan Tun Zaw, VP of Business Development, Athena Dynamics
Introduction
“What are data diodes?”, “What is the purpose of data diodes?”, “How do data diodes work?” Pertaining to data diodes, people today often have a plethora of questions regarding the various aspects and functions of them. Data diodes play an integral part in safeguarding networks and information transferred between them. Yet, they remain often misunderstood by many despite their important purpose in today’s world where digitization has taken the front seat. As such, this article attempts to explain all about data diodes and the aforementioned questions in a simple, concise manner in order to demystify them.
What are data diodes?
In order to best explain what data diodes are, one must first understand what a diode is. Diodes are electrical components which allow current to only travel in one direction in a circuit. Diodes are often depicted in circuits as a triangle together with a vertical line, which it is pointing to and touching. The side with the triangle is known as the anode which is the positive terminal whereas the side with the vertical line is known as the cathode, which is the negative terminal. Theoretically, the positive side of the diode has zero resistance whereas the resistance on the negative side is infinitely high. As such, current is only able to flow from the positive to the negative terminals and not the opposite direction as the infinitely high resistance prevents electrons from flowing in the opposite direction.
Similarly, in terms of their function, data diodes are hardware devices which allow for the one-way transfer of data and information. However, though similar in function to unidirectional security gateways, data diodes are not necessarily the same and should not be confused with them. Unidirectional security gateways can sometimes be sophisticated combination of uni-directional technology and hardware allowing for bi-directional data transfer for specific use cases whereas data diodes themselves are simply uni-directional hardware solutions.
Why and How are data diodes used?
Typically, data diodes are placed between 2 networks of differing security levels, one being more secure and the other having a lower security level. Such systems are separated in order to protect highly sensitive data, which is known as an air gapped network. This often takes place in a military or in critical networks which will be further elaborated on later. Traditionally, organizations used portable media like USBs or DVDs to transfer data across the segregated networks but this would make the purpose of segregating the networks self-defeating since the malicious software can be spread through the removable media. However, the requirement for data exchange between such segregated systems is rising, and as such a huge security risk arises from such data exchange.
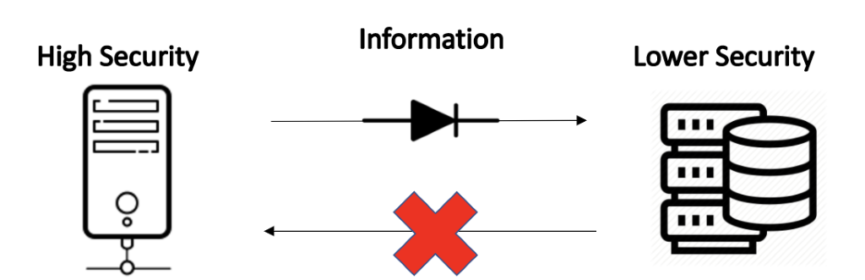
A data diode placed between these two networks ensures that data flow remains possible, albeit in a single direction. This in turn preserves the integrity of the networks by preventing the leakage of any sensitive data. Data diodes are typically used in two different scenarios.
Firstly, when information is transferred from a network of higher security to a network of lower security. Such data transfer occurs when operators of the network require the data for certain processes such as auditing or for an analysis. The presence of a data diode when information is transferred from the more secured network to the less secured network ensures that data can only travel in a single direction and that no malicious actor is able to take advantage of the connection in the opposite direction to access the more secure network in order to manipulate it. This safeguards the information in the more secure server, bolstering its security.
Secondly, data diodes are also used when data is transferred from a network of lower security to a network of higher security. This enables information to be collected from the lower security network, compiled, and sent back to the higher security network. As such, no sensitive data can be compromised and leaked through the same channel, thus keeping the networks safe.
Going on to the next point, which is explaining how data diodes function and work, here is an analogy. Think of a water pipe. Water can flow in either direction within the pipe. Now add a one-way valve in the pipe. Water is now only able to flow in a single direction. Think of a diode as a valve with the main parts of the diode being parts of the valve. There is a transmitter on one end and a receiver on the other end. Data is transmitted from the transmitter and received by the receiver. It is physically unable to go in the opposite direction. This can also be achieved through the send and receive transceivers in a data transfer cable being disabled in one direction and any link failure protection systems being disabled. Meanwhile, proxies in the network interface of data diodes allow for two-way communication to continue unhindered on each side of the data diode.
Why are data diodes so effective?
Data diodes are referred to as one of the most robust cybersecurity solutions available on the market. Some cybersecurity analysts even claim that the only solution better than a data diode would be to ensure that there is a physical air gap and no interactions between the two segments at all. This means forcefully segregating and partitioning the networks so no connections to other networks remain. This is usually unfeasible and counterintuitive as productivity may be affected with the lack of information transfer, as briefly touched on in part B. Data diodes are also physical solutions and are not software, configuration-based solutions. The sheer impossibility of overcoming and manipulating a data diode remotely, due to the fact that it is assured on the physical level (i.e. The TX can only transmit and the RX can only receive the electrical signal), makes it one of the safest ways for cross-domain data transfer. Now, the article will explain more about the benefits of data diodes.
Benefits of Data Diodes
As mentioned earlier, manipulating a data diode today is practically impossible unless there is a physical invasion on the devices themselves. As such there have been extremely low cases of any data diodes being compromised thus far. Theoretically, the most common way data diodes can be “compromised” is when, due to possible misconfigurations in the network, causing the two assets on both sides of the network to bypass the data diode.
Furthermore, most cyberattacks in today’s world require and rely on two-way traffic, and by restricting traffic in a single direction, this enables most attacks of such sort to be averted, preventing the malware from calling back its Command & Control server. Additionally, data diodes have relatively lower long term operating costs compared to traditional software-based solutions due to the reduced need for updates or maintenance, as mentioned in a report by the SANS Institute.
Disadvantages of Data Diodes
Traditionally, the lack of flexibility of data diodes which is touted as one of its benefits can also be seen as a major flaw for certain users. Data diodes typically only have a single use which is to restrict traffic, resulting in unidirectional data flow, and this limits their uses. Luckily, this may not necessarily be the case today where multiple data diodes can be used in tandem with cloud software and firewalls to increase flexibility and enable multi directional data transfer.
Data diodes, especially industrial ones can be relatively expensive, with the price going into 6 digits. This is potentially cost prohibitive for most corporations and combined together with their lack of flexibility, many will hesitate before making use of them. Data diodes also necessitate specialized skills and knowledge to install, a skillset which is not generally available in the mass market.
Why use a data diode over a firewall?
Both firewalls and data diodes function similarly, which is to filter and block malicious traffic. On the contrary, compared to data diodes, firewalls are more adaptable and flexible. They are also frequently used and well understood by many people. Furthermore, they have relatively cheaper installation costs. However, the flexibility of firewalls may very well be its own Archille’s heel. The flexibility of firewalls is due to them being software-based solutions allow for traffic to be filter both ways and to be directed to several different servers. This makes firewalls and the servers susceptible to complex, coordinated attacks which may be able to bypass it to access the servers. Zero-day exploits, which are newly engineered flaws will also not be detected by the firewall and be able to pass through undetected. This is proven by the fact that even the most well-known firewalls by huge corporations has tons of CVEs reported every year. This is unlike data diodes which stops all traffic coming from the opposing direction, regardless of whether it is malicious or not. Likewise, being a software-based solution, firewalls have significantly higher long term operating costs as there is a need to maintain the rules, firmware and to release updates and patches constantly.
What kind of different data diode technologies are there and what type of forms do they exist in?
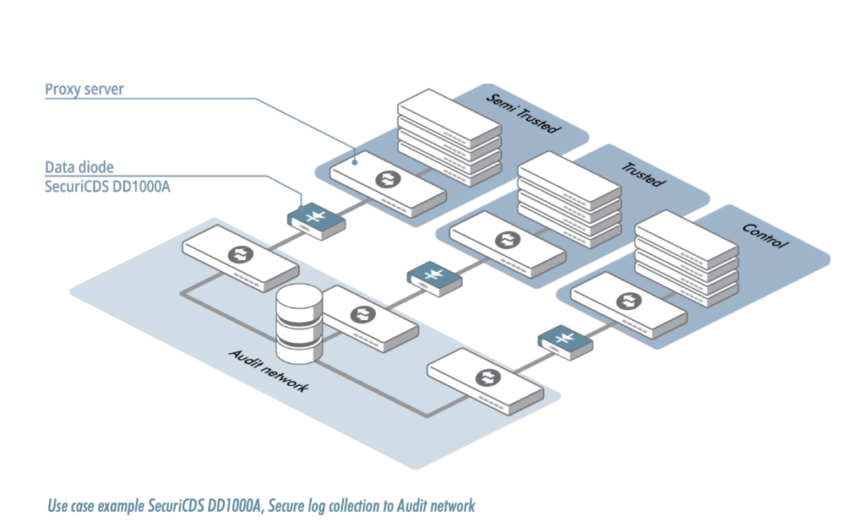
The data diode technologies which commonly exist today are hardware; optical fiber; optical; electrical and electromagnetic. The most commonly found types of data diode technologies today would be just hardware and optical, consisting of a modified optical cable. However, some data diodes contain software such as proxy servers which can be then configured. Such technologies can be found in different configurations, mostly rack mounted; DIN rail or in standalone form. Rack mounted and DIN rail data diodes are more commonplace as they can be conveniently mounted in a rack inside a server room. This ensures that they remain near the servers which they are connected to.

Where can data diodes be found? What are some common case studies for data diodes?
The use of data diodes started out in earnest in the military sector. Many militaries still make use of data diodes to keep sensitive information safe and out of the wrong hands. This enables files of lower security classification (restricted) to be transferred between servers without compromising other files of higher security classification. (Such as Classified and Top Secret). Such data transfer may also be required for auditing purposes. Data diodes used in a military setting require more rigorous certification due to the sensitive nature of the information being handled.
Governments around the world also commonly make use of data diodes today. A common case study would be to allow the transfer of software patches into a secure network while ensuring the remaining stored information will not be tampered with and altered, since such data cannot be accessed in the opposite direction by taking advantage of the connection. Law-enforcement and intelligence agencies also make use of data diodes to secure information or footage gathered through tools such as cameras and listening devices. This reduces the likelihood of any sensitive information gathered leaking out.
Likewise, many sectors with critical infrastructure also make use of data diodes to safeguard them. These sectors include utilities (traditional power plants, nuclear power plants, oil and gas refineries), transportation (rail or aerospace) and telecommunications. Such critical infrastructure sectors rely on other external IT systems and third parties for managing and gaining information. This makes them more vulnerable to cyberattacks.
A potential cyberattack against any of these sectors could be debilitating, potentially crippling essential services which many people rely on. Such providers of essential services or managers of critical infrastructure therefore cannot afford to suffer from such an attack. The managers of such infrastructure need to strike a balance between security and the need to retain efficiency, to guarantee operational uptime. As such data diodes are used by these providers.
To Conclude
In summary, data diodes are not as complex and mysterious as some people think they are. They have a relatively simple operating principle and a single purpose – to ensure that data and information only travels in a single direction. They have a proven track record in terms or reliability and security. Notwithstanding their disadvantages, I feel that the benefits of data diodes far outweigh that of their disadvantages, and this is a sentiment agreed by many governments and armed forces today, with even the US Department of Homeland security legislating their use in critical infrastructure. With such legislature requiring their use coupled with increasing demand and manufacturing capabilities, one can expect their prices to drop in the future and for their usage to become more commonplace.
How can you protect yourself with a data diode today?
A data diode itself is a foolproof strong solution against cyberattacks. However, one also requires the relevant expertise to install and provide service for the data diodes. At Athena Dynamics, we have two renown and reliable brands of data diode solutions available for clients. Unlike other data diode providers, the data diodes we offer are cost effective, with convenient installation times. Both data diode offerings have their own distinct functions, uses and configurations, allowing us to meet the wide range of requirements which most customers have.
Gatescanner Injector
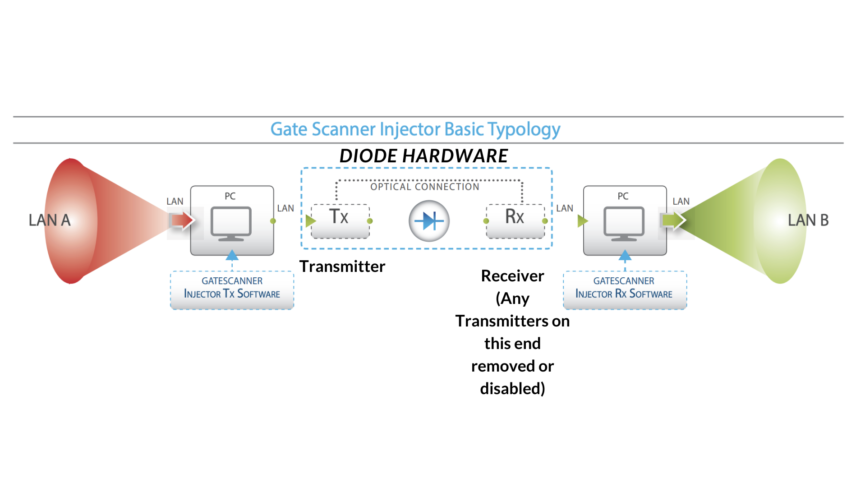
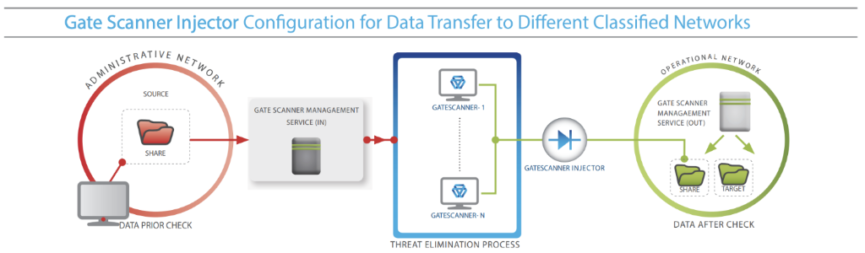
GateScanner Injector is a Windows–based data diode which comes in a modular form. Developed by Sasa Software, an Israeli Cybersecurity Firm Specializing in CDR (Content Disarm and Recovery) solutions, the company has also been recognised by Gartner® as ‘Cool Vendor in Cyber-Physical Systems Security’ (2020). Sasa Software is subsidiary of Plasan, a major armored vehicle contractor for the US Military. GateScanner Injector was developed mainly to complete the GateScanner solution suite, which offers client an integrated process of scanning and transferring files into a network. These diodes are also fully integrated and intended for use with their CDR (Content Disarm and Reconstruction) technology modules. They are bundled with transmitting and receiving software to ensure the data entering and exiting the diode is threat-free.

Advenica SecuriCDS
SecuriCDS is a line of Linux-based diodes offered by Swedish cybersecurity specialists Advenica, which are listed on the Nasdaq Stockholm (Swedish) stock exchange. Their data diodes typically come in rack-mounted, all-in-one configurations enabling their flexible usage.
Advenica also has Unidirectional Security gateway offerings which allow for bi–directional data transfer. Their diodes also come with proxy servers as standard, with some having the option to set up one’s own custom proxy services. These diodes are certified by many governments and armed forces, including the EU and the Swedish Armed forces.

Biographies

Bryan Lim is an Associate (Intern) in the business development team in Athena Dynamics Pte Ltd, a subsidiary of BH Global Corporation Ltd, a company listed on the Singapore Stock Exchange (SGX).
Contact: [email protected]

Nyan Tun Zaw is the VP of Business Development at Athena Dynamics Pte Ltd, which is a subsidiary of BH Global Corporation Ltd, an SGX mainboard listed company.
With a wide range of background in cybersecurity, software development, web development as well as networking, Zaw has in-depth experiences in deploying security solutions for several highly confidential government and critical infrastructure projects, particularly in the CDR/CDNR field as a technical lead. His interest mainly lies in Cybersecurity and AIML.
Zaw holds a Bachelor of Business Management, with double majors in Finance and Information Systems, from Singapore Management University as well as Master of Business Administration (MBA) from Quantic School of Business and Technology. He is also a holder of the Certified Ethical Hacker (CEH) and EC-council Certified Security Analyst (ECSA) certificates.
Being a technical person who also likes sharing his experiences and knowledge, Zaw has also been part of a speaking panels with global C-level executives at various events and conferences in the region.
Contact: [email protected]
Disclaimer: Neither BH Global, Athena Dynamics nor the writer guarantees full and timely accuracy of the write-up. Readers shall read with their own discretion, judgement and research if in doubt. If you wish to contribute further writings, please feel free to contact us.
Not for General Distribution. Copyright © 2021 All Rights Reserved. No part of this presentation materials may be distributed/reproduced without the writers’ expressed consent.
References
- “Data Diodes” – Advenica. Retrieved 3 March 2021
- “Learn About Data Diodes” – Owl Cyber Defence. Retrieved 3 March 2021
- Krum & Owl CyberDefence, 2018, “What is a data diode and how do data diodes work?” – Retrieved 5th March 2021
- “Data Diode Cybersecurity products” – Owl Cyber Defence. Retrieved 3 March 2021
- “What’s the difference between Data Diodes & Firewalls? – White Paper OWL Cyber Defence” (PDF)
- “GateScanner Injector Software – Sasa-Software.com ” (PDF)
- “What is a Data Diode and how does it work?” – Advenica. Retrieved 4 March 2021
- “Data Diode Case studies” – Nexor. Retrieved 4 March 2021
- Slay, J & Turnbull, B 2004, ‘The Uses and Limitations of Unidirectional Network Bridges in a Secure Electronic Commerce Environment’, paper presented at the INC 2004 Conference, Plymouth, UK, 6–9 July 2004 – Retrieved 4th March 2021
- “SANS Institute Tactical Data Diodes in Industrial Automation and Control Systems”. Retrieved 4th March 2021
- Okhravi, Fredrick T.Scheldon, 2010, “Data Diodes in Support of Trustworthy Cyber Infrastructure”, paper published at the Massachusets Institute of Technology Lincoln Laboratory – Retrieved 8th March 2021
- “Improving Industrial Control System Cybersecurity with Defense-in-Depth Strategies – United States Department of Homeland Security” (pdf)
- “Can you use malware to bypass a data diode system with radio waves?” – Fox IT Group – Retrieved 15 March 2021
- Tomlinson & M. Elkins 2019, ‘Trying to break the “unbreakable” ‘, article published for Archer News Network – Retrieved 15 March 2021
- “Secure Network Separation” – sasa-software.com – Retrieved 23 March 2021

