
Young Writer Series – Email Security
Young Writer Series – Email Security

Author: Koh Kai Xun, Cybersecurity Intern, Athena Dynamics
Copyright © April 2024 All Rights Reserved Athena Dynamics Pte Ltd
Advisory Editor: Terrence Tan, Solutions Architect & Technology Strategist. Athena Dynamics
Introduction
Google and Yahoo recently announced new email requirements that would take effect from February 2024. All senders must have either SPF or DKIM email authentication set up for their domain. Senders who send more than 5,000 messages per day to Gmail accounts must set up both SPF and DKIM email authentication and have DMARC policies. But what exactly do these authentication protocols entail?
Before we delve into these protocols, however, we must first understand how emails work and what is happening under the hood of one of the most widespread forms of communication in our everyday lives.
The journey of an email
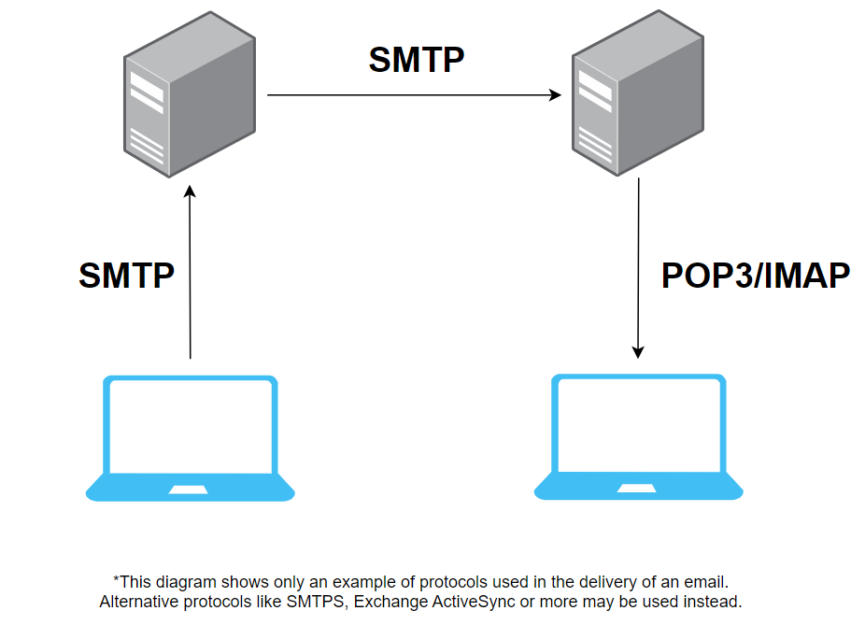
From a high-level point of view, the journey of an email begins with it being sent from a user to his or her mail server. The mail server then sends this email, through the internet, to the recipient’s mail server where it would eventually arrive in the recipient’s inbox.
Basic Email Concepts
But what exactly is happening behind the scenes?
SMTP
Simple Mail Transfer Protocol (SMTP) is a widely used communication protocol responsible for the transmission of emails through the internet. SMTP uses a simple message format where the email content is transmitted as plain text. The email includes header fields (e.g. From, To, Subject) and the body of the message. If the email is undeliverable for whatever reason, SMTP returns it to the sender and notifies him or her that the email address used was incorrect or the recipient mail server rejected the email.
Meanwhile, communication between users and their mail servers uses another protocol. POP3 and IMAP are email retrieval protocols employed by mail clients (users) to retrieve emails from the mail server. Let us take a quick look below.
POP3
Post Office Protocol 3 (POP3) downloads the original emails from the mail server on a single device before deleting the emails from the mail server. While this allows for offline access of emails files, the downside is that all data would be lost should anything happen to the device. Furthermore, deleting the original email from the server results in the fact that several devices cannot access the same email. Thus, this protocol would be more suitable for users who tend to access their emails with only one device. Of course these days, most email clients also offer an option to “Leave message copy on the server”. This will allow other devices to access the same mail also.
IMAP
Internet Message Access Protocol (IMAP), on the other hand, is the most commonly used email retrieval protocol. It retrieves data from the mail server and caches said data locally on the device. Hence, users can access the same email across multiple devices since all data is kept on the mail server rather than the local device. The disadvantage of this approach, however, is that access of uncached data or changes made to cached data would mean syncing with the mail server which requires a stable internet connection. This also places a larger strain on the server since everything is stored there instead of the local device.
Email Security Protocols
Now that we have a better understanding of how emails are sent from one point to another, we are ready to dive into the various protocols that have been designed to keep this entire process safe and secure.
SPF
Sender Policy Framework (SPF) is an email authentication method that helps recognise the mail servers approved to send email for a given domain. This list of allowed mail servers is saved as an SPF record in the Domain Name System (DNS) which can be queried for by recipient mail servers.
DKIM
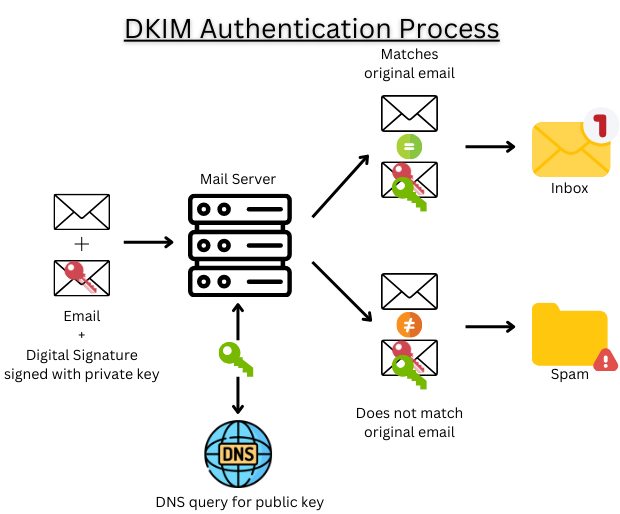
Domain Keys Identified Mail (DKIM) is another email authentication protocol that is designed to fight against email spoofing and spam. This can be done by adding a digital signature to outgoing messages. The digital signature allows the recipient’s email server to verify that the email actually came from the sender it claims to be sent from.
When DKIM is first enabled, an asymmetric key pair is created which includes a private and a public key. The private key is kept securely by the recipient, whereas the sender’s public key is published in the domain’s DNS records.
Digital signatures are created by signing the email content with the sender’s private key. This signature is added to the email header, which is invisible to the recipient. The recipient of the email can obtain the sender’s public key through a DNS query and use it to verify the email’s digital signature.
Imagine you’re sending a package. Normally, anyone could put any label on it and claim it’s from you. That’s how email spoofing works – attackers sending emails pretending to be someone else. DKIM is like a special security seal on your package. It’s a hidden code created with your private key, like a unique signature. When the recipient gets the package, they can use a matching public key (available for everyone) to check if this seal is real.
If the seal matches, it proves the package truly came from you and not someone else, meaning the email is likely legitimate! If the seal is wrong or missing, it means someone tampered with the package or faked the label, meaning the email is suspicious!
This helps email servers know which emails are truly from you and which ones are not. Think of it as a way to build trust and make sure your emails actually reach people’s inboxes, not their spam folders!
SPF and DKIM’s limitations
However, both these methods have their own limitations (which could be exploited!).
- SPF does not verify the easily spoofed “From:” header visible to users in emails. If the attacker sent an email from an allowed mail server that passed SPF checks, he or she would be able to place an email in the user’s inbox claiming to be from someone else. From there, it would only be too easy for the user to mistake the email for one from a legitimate source.
- DKIM only guarantees the integrity of an email. It does not verify that the contents of the email are safe. What this means is that an attacker can create an email from any trustworthy domain, send an email containing anything to the victim and still pass DKIM checks.
DMARC
These limitations are why we need Domain-based Message Authentication, Reporting, and Conformance (DMARC). DMARC is an email authentication protocol that builds on SPF and DKIM to enhance email security. It consists of a set of policies that specify what should be done for emails that fail security mechanism checks like SPF or DKIM.
There are 3 possible types of policy settings:
- None (monitoring mode): DMARC is set to monitor or report only. No action is taken against emails that fail authentication checks and a report is sent to the domain owner.
- Quarantine: Email receivers treat messages that fail DMARC checks as potentially suspicious. Such messages may be placed in the recipient’s spam or quarantine folder. However, they shared that this adds ambiguity to the system as the ball is now in the user’s court and is up to them to do what they want with this suspicious mail.
- Reject: Emails failing DMARC checks are rejected outright and will not turn up in the recipient’s inbox at all.
So how does SPF and DKIM work together in DMARC to ensure email security? Imagine email addresses like street addresses and your mailbox as your email server. SPF is like checking who’s allowed to use your mailbox: You put a list of approved mail carriers (authorised email servers) outside your house (DNS records). Anyone else trying to deliver mail using your address looks suspicious.
DKIM is like sealing your mail with a unique stamp. You have a special stamp only you can use (private key). You stamp your outgoing mail with it (digital signature). The recipient checks if the stamp matches a public copy you have outside (public key). If the stamp matches, your mail is authentic!
Together, they fight email impersonation. SPF prevents others from sending mail like it’s from you (address check). DKIM ensures the mail actually came from you (stamp verification). This helps stop fake emails pretending to be you, keep spam out of your inbox and others’ and get your emails delivered instead of blocked as suspicious.
So, SPF checks the “address” while DKIM checks the “seal” of your email, working together to ensure it’s truly from you!
The road ahead

As was stated above, Google and Yahoo have been rolling out their new guidelines. Since their announcement, Google has also clarified about what would happen to those who fail to meet these requirements:
- Bulk senders (more than 5000 messages per day to Gmail accounts) will start receiving SMTP temporary errors on some of their non-compliant email traffic.
-
- If left unchanged, a certain percentage of this non-compliant email traffic would soon begin to be rejected, with the rejection rate set to increase as time passes.
- This will significantly impact the deliverability of the emails from non-compliant companies which would then translate into an even greater impact on their businesses.
While there appears to have been a shift in emphasis towards DMARC, DMARC still presents its own set of challenges. Domains without DMARC trying to send mail to domains that do would have to implement DMARC as well. In the wake of Google and Yahoo’s announcement, Microsoft has been urging Microsoft 365 users to implement SPF, DKIM and DMARC. This is to ensure that emails sent to such DMARC-implemented domains are delivered and not blocked or flagged as spam. What this entails for domain administrators is more work required to add SPF records and generate the asymmetric key pair for their domain. This is just the tip of the iceberg of the ripple effect caused by Google and Yahoo’s decision.
Conclusion
2023 saw a steep 222% increase in email-based attacks with more advanced tools like AI being used. And while there may exist countless email security solutions out there, DMARC remains as the foundation of which companies and users should build their email security measures upon. As even mainstream email domains begin enforcing these security measures, it is increasingly crucial that we do the same across all our emails to better safeguard ourselves against the ever evolving threats in the world.
Bibliography
- Kumaran, N. (2023, October 3). New Gmail protections for a safer, less spammy inbox. Google. https://blog.google/products/gmail/gmail-security-authentication-spam-protection/
- Gupta, P. (2023b, June 27). Checking phishing mail by SPF, DKIM, and DMARC – Pradeep Gupta – medium. Medium. https://medium.com/@pradeepgupta_9558/checking-phishing-mail-by-spf-dkim-and-dmarc-b176de45d50d
- Yahoo-Postmaster. (2023, October 3). More Secure, Less Spam: Enforcing Email Standards for a Better Experience. Tumblr. https://blog.postmaster.yahooinc.com/post/730172167494483968/more-secure-less-spam
- Tyler, N. (2024, February 8). 222% surge in email attacks during 2023. New Electronics. https://www.newelectronics.co.uk/content/blogs/222-surge-in-email-attacks-during-2023/


